Create an effective incident response (IR) plan to mitigate the impact of cyberattacks

When it comes to modern cybersecurity, protection is only half of the equation. Business leaders must assume that they will, at some point, fall victim to a security incident. When that happens, a coordinated, cross-functional team will need to move fast to minimize the damage.
A strong incident response (IR) plan is key to detecting, responding to, and managing security incidents in a timely manner and rapidly returning technologies, processes, and staff to normal operations, and IR has become increasingly fundamental as the sophistication and severity of cyberattacks push the cost of cybersecurity incidents to new highs.
CohnReznick’s Cybersecurity, Technology Risk, and Privacy practice combines leading risk-management and security processes and technologies to create a tailored IR program based on your specific needs, making it easier to safeguard your sensitive data, intellectual property, and brand reputation, as well as meet compliance and regulatory obligations.
The benefits of a clear and coordinated IR program
- An established and tested IR program, coupled with business continuity and disaster recovery plans, will help improve incident response time and resiliency. These programs enable organizations to:
- Rapidly take action to remediate an incident
- Better triage reported and detected security events
- Comply with any applicable compliance or regulatory requirements and align with industry standards and frameworks
- Establish processes to coordinate the response effort across teams and functions, including business unit stakeholders, management, and legal
- Provide clear documentation of IR processes, roles, and responsibilities
- Promote a culture of security and data privacy across the organization
- Increase awareness of other potential cybersecurity threats facing the organization
- Strengthen communication with executive leaders on security incidents to gain buy-in and support for strategic decisions and remediation efforts
- Foster a culture of continuous improvement based on “lessons learned”
4 phases of incident response
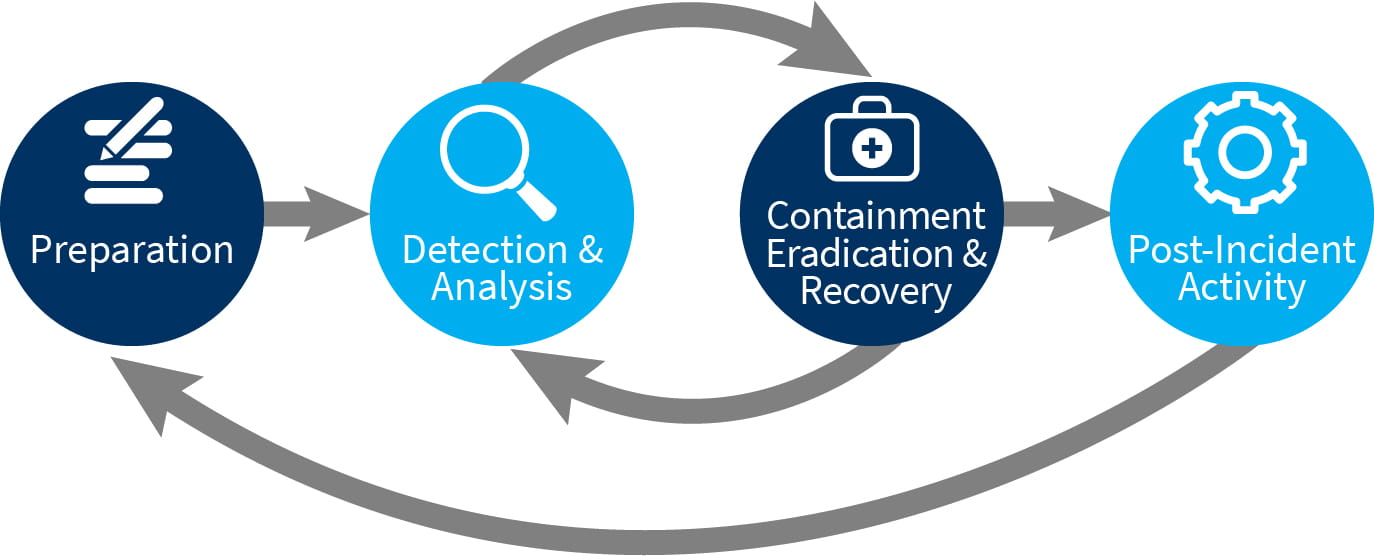
Leading IR programs are often based on the National Institute of Standards and Technology (NIST) Computer Security Incident Handling Guide (NIST Special Publication 800-61). We help organizations develop programs that follow its four-phase approach:
Preparation: Establish responsibilities and objectives. Regularly assess systems and applications for risks. Understand, prioritize, and mitigate threats. Identify and monitor critical resources; understand baseline/normal operations and behavior. Train and equip employees to respond to incidents.
Detection: Monitor computer security software alerts, logs, publicly available information, and people for precursors of a future attack and indicators of an ongoing or completed attack. Analyze, validate, document, and prioritize incidents and take appropriate action (including notification of key parties).
Containment, Eradication, and Recovery: Respond to attacks before they cause significant damage. Isolate affected systems for analysis, eliminate components of the incident (e.g., malware, account breaches), block communications with the attacker, and identify vulnerabilities for remediation. Gather and document evidence. Restore systems to normal operation and implement changes to prevent future incidents. Identify the attacker.
Post-Incident Activity: Learn from previous incidents. Review attacks, responses, and metrics, and identify improvements. Retain evidence and update IR plans.
Communications and employee training are essential
The responsibility for incident response is not solely that of the IT function. An effective IR program must be developed and communicated across the entire organization – and led by senior management.
It is vital that there be an ongoing commitment to user security training and awareness. Tabletop exercises and drills can help reinforce steps and processes that all stakeholders – C-suite executives, third parties, IT admins, and program leaders – will need to take in remediating an incident.
CohnReznick IR services
- Incident response assessment
- Incident response plan development and implementation
- Incident response as a service
- Business continuity management
- Disaster recovery planning
- Notification requirements
- IR tabletop exercises and periodic training
Why CohnReznick stands apart
At CohnReznick, our goal is to help you establish a clear plan for incident response based on your specific risks and individual business strategy, and to confirm that plan is validated, tested, effective, and aligned with your other policies and programs (e.g., business continuity, disaster recovery, crisis management, and emergency communications). Our IR teams have deep experience across industries and help develop and implement IR programs that enable quick action to minimize damages. Our cybersecurity risk management specialists have in-depth knowledge of regulatory requirements and the evolving response of regulators to help you maintain compliance – even in the event of a breach. Plus, we work with an array of solution providers to help address specific needs for technology, solutions, and recovery platforms.Contact
Bhavesh Vadhani, Principal, Global Leader, Cybersecurity, Privacy, and Technology Risk
703.847.4418
Thomas McDermott, Principal, Cybersecurity, Privacy, and Technology Risk
973.364.7836
Ali Khraibani, Senior Manager, Cybersecurity, Privacy, and Technology Risk
862.245.5166
Contact
Let’s start a conversation about your company’s strategic goals and vision for the future.
Please fill all required fields*
Please verify your information and check to see if all require fields have been filled in.

The C-Suite Dashboard Keep Your Business Moving Forward
Related services
This has been prepared for information purposes and general guidance only and does not constitute legal or professional advice. You should not act upon the information contained in this publication without obtaining specific professional advice. No representation or warranty (express or implied) is made as to the accuracy or completeness of the information contained in this publication, and CohnReznick, its partners, employees and agents accept no liability, and disclaim all responsibility, for the consequences of you or anyone else acting, or refraining to act, in reliance on the information contained in this publication or for any decision based on it.



















