Support rapid delivery of secure software with DevSecOps

As digital transformation and enterprise cybersecurity technologies continue to advance – along with the cyberthreats that challenge them – so too does the need to adopt robust tools and techniques for secure, rapid software development. Organizations face challenges not only in preventing the introduction of vulnerabilities during development but also in ensuring that deployments are secure and compliant.
That’s where DevSecOps can help. A mix of development, security, and operations, DevSecOps is a process that integrates security into every phase of software development, from initial design to delivery. Traditionally, security has often been “bolted on” to software, almost as an afterthought, at the end of the development cycle. But as developers began using Agile and DevOps development methods, this after-the-fact implementation of security created bottlenecks in software delivery and introduced issues with functionality. DevSecOps, by contrast, addresses security issues as they occur.
A transition to DevSecOps will entail more than just implementing automated security tools, however. This development model aims to help businesses proactively anticipate, rather than simply respond to, data security incidents. To that end, security is built into all phases of the development lifecycle to help reduce the costs associated with addressing security flaws.
Other benefits can include:
- Continuous delivery of software in an abbreviated development lifecycle
- Automated software builds and testing
- Rapid response to change requests and needs
- Improved communication and collaboration across teams
- Early identification and resolution of code security vulnerabilities
- Lower costs of repairing security flaws
- Fewer deployment issues
- More rapid recovery from failure
If you’re considering adoption of DevSecOps, you’ll need to first understand the evolution of software development. As the saying goes, “You can’t know where you’re going until you know where you’ve been.”
The evolution of software development
Over the past two decades, software development processes have evolved from traditional linear approaches like the Waterfall method to more iterative approaches that allow developers to continually test for flaws. Following is a brief overview of software development approaches:
Waterfall: This model consists of sequential phases (such as requirement gathering, design, development, testing, and maintenance) in which the next stage cannot begin until the previous stage is completed. Because the Waterfall methodology follows a strict sequence of software development, any unplanned adjustments at the end of the development process can lead to challenges and delays.
Agile: The Agile model replaces the Waterfall’s strict sequences with continuous, iterative development and testing throughout the software development lifecycle (SDLC), executed by cross-functional teams. The most popular Agile framework, Scrum, focuses on delivery cadences called sprints and a meetings structure that includes planning, review of backlog items, and daily stand-up sessions.
DevOps: Through a combination of people, processes, and technologies, DevOps enables continuous integration and software delivery. DevOps represents a cultural shift over its predecessors. While Waterfall is linear and Agile organizes project activities into distinct phases, DevOps automates and integrates processes among software development and IT teams, which enables them to release software faster.
DevSecOps: Taking DevOps one step further, DevSecOps integrates security into DevOps processes, bringing them together in a collaborative culture. The objective is to strengthen application security by introducing a variety of security techniques early in the development process, rather than after product release, which can help reduce the number of flaws that make it that far and thus the costs of fixing them. Development teams are enabled to execute security tasks independently.
As the paradigm shifts, strong security becomes a key deliverable.
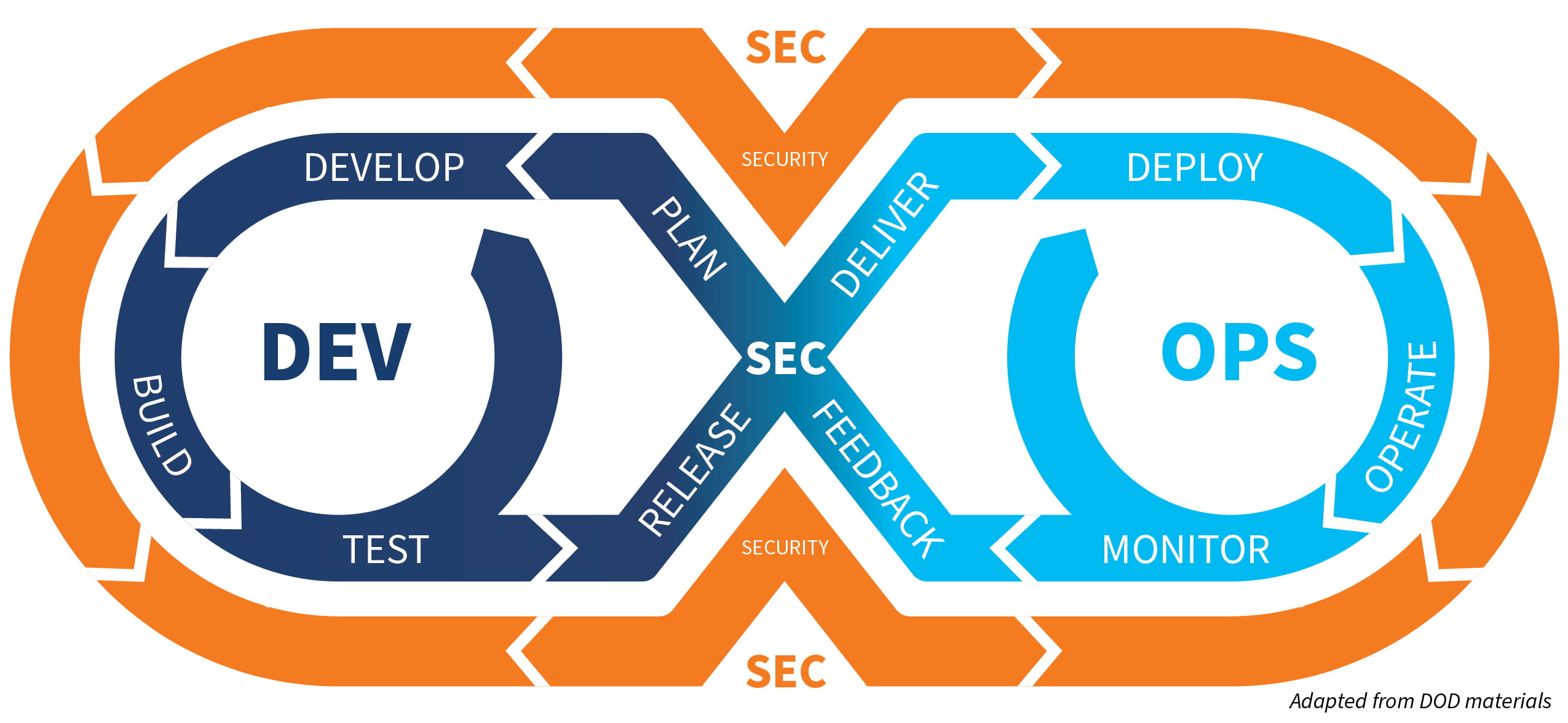
7 steps for making the move to DevSecOps
Adoption of DevSecOps will require that you carefully consider a number of operational, technology, and employee knowledge factors. Steps in this transition include:
1. Define and implement security requirements during the design and development phases.
2. Implement a mechanism to monitor high-risk application deliveries while fast-tracking delivery of low-risk applications.
3. Select and implement automation and security scanning tools that meet the needs of your current environment, and use them for every development.
4. Integrate automated approval workflow throughout the change-management process.
5. Perform secure code reviews for every software deployment.
6. Provide security training for developers and code training for security professionals.
7. Develop security awareness and a collaborative culture in which staff feel comfortable reporting continuous feedback or potential anomalies.
In conclusion
At its core, DevSecOps is less about implementation of security tools and more about the combination of culture, development, policy enforcement, automation, and integrations of security requirements and considerations across the development lifecycle. You cannot realize productivity gains at the expense of strong security practices. The costs, resources, and reputational impacts associated with a security breach can easily outweigh any perceived efficiencies associated with omitting security from your development methodology.
Striking the right balance between innovation and management of related risks will require that businesses regularly reassess their existing development processes, technologies, and controls. Designing a tailored approach for transitioning to DevSecOps and regular risk assessments should be front and center in an organization’s path forward.
Contact
Bhavesh Vadhani, CISA, CRISC, CGEIT, PMP, CDPSE, Principal, Global Leader, Cybersecurity, Technology Risk, and Privacy
703.847.4418
Thomas McDermott, CISA, CRISC, CGEIT, Principal, CohnReznick Advisory
973.364.7836
Tauseef Shaikh, Manager, Cybersecurity, Technology Risk, and Privacy
862.245.5115
Contact
Let’s start a conversation about your company’s strategic goals and vision for the future.
Please fill all required fields*
Please verify your information and check to see if all require fields have been filled in.
Related services
This has been prepared for information purposes and general guidance only and does not constitute legal or professional advice. You should not act upon the information contained in this publication without obtaining specific professional advice. No representation or warranty (express or implied) is made as to the accuracy or completeness of the information contained in this publication, and CohnReznick, its partners, employees and agents accept no liability, and disclaim all responsibility, for the consequences of you or anyone else acting, or refraining to act, in reliance on the information contained in this publication or for any decision based on it.


















