Maintain DFARS Cybersecurity Compliance with Advanced Technology Solutions
Cyber-attacks on organizations, including government contractors and federal agencies, have been rapidly increasing over time. With a lack of defined security policies, processes, and controls, many government contractors are ill-equipped to effectively handle potential cyber-attacks that could severely undermine business operations and swiftly lead to insurmountable damages as data and records are destroyed.
To mitigate the risk that businesses face, cybersecurity standards are becoming more prevalent. In particular, organizations with government contracts need to demonstrate compliance with cybersecurity standards as specified in contract requirements and regulations. For example, defense contractors that provide services to Department of Defense (DoD) agencies related to building, maintaining, and managing DoD systems, networks, programs, or data may be required to demonstrate compliance with Defense Federal Acquisition Regulation Supplement (DFARS) Safeguarding rules and clauses.
In 2015, the DoD issued a ruling that requires defense contractors and subcontractors to demonstrate cybersecurity compliance with regard to the protection of Covered Defense Information (CDI), also known as Controlled Unclassified Information (CUI), or Unclassified Controlled Technical Information (UCTI).
How Can A Defense Contractor Demonstrate DFARS Clause Compliance?
Defense contractors and sub-contractors must implement and continuously assess security requirements, thereby demonstrating adequate cybersecurity measures are in place to safeguard CDI information from unauthorized access and disclosure. Additionally, such security measures can help identify, prevent, detect, and report cyber-related intrusion events that affect defense contractors’ unclassified information systems. The security requirements are specified in National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171, “Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations.”
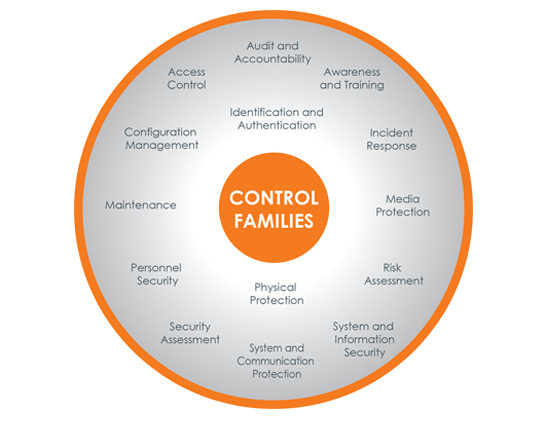
Security requirements are categorized into 14 control families as listed in the graphic to the right. In addition to implementing the 14 security requirements, defense contractors and sub-contractors must have processes in place to identify a cybersecurity incident and report the incident no later than 72 hours upon discovery of the incident/breach. Reporting of the incident requires addressing elements, as outlined on the cyber incident reporting form, and providing necessary supporting documentation and evidence related to the incident. The incident can only be reported using a DoD-approved medium assurance certificate.
PAIR DFARS COMPLIANCE ASSESSMENT WITH ADVANCED BREACH DETECTION SOLUTIONS
A critical component of DFARS regulation, as well as an area where we have found contractors to continually lack capabilities, is in breach detection. That is why it is important to have advanced solutions combined with appropriate governance and mature processes to enable contractors to rapidly detect devices of interest and indicators of compromise (IOC).
CohnReznick utilizes a holistic solution designed explicitly to fill this gap with clients. Our solutions can analyze thousands of protocols and hundreds of new attack vectors each day to find breaches and anomalous behavior on the defense contractor network. X-ray visibility into your environment is achieved by continuously analyzing application-based metadata―combined with user information and the latest threat intelligence, against past, current, and future network activity―to detect any previously unidentified breaches. Defense contractors and sub-contractors can be assured of accelerated compliance with DFARS requirements for incident response, risk assessment, and system and communications protection.
Moreover, IOCs and compromised device behavior can be pinpointed through behavioral analysis conducted on the network communications. Such IOCs and compromised device behavior could include:
What If I Can’t Demonstrate DFARS Clause Compliance?
The defense contractor is required to notify the DoD CIO within 30 days of contract award if the defense contractor and their sub-contractors are not in compliance with all of the security requirements. Contractors have until December 2017 to attain compliance with all of the security requirements in NIST SP 800-171. Non-compliance can lead to cure notices, adverse past performance, fee reduction penalties, and possibly civil False Claims Act (FCA) implications, as well as reputational risk and responsibility issues, which could lead to loss of awards.

ABOUT COHNREZNICK’S TECHNOLOGY RISK AND CYBERSECURITY SERVICES
CohnReznick provides cybersecurity solutions that are dynamic, scalable, and tailored for growth companies. CohnReznick’s security professionals average more than 15 years in the field and hold key certifications. Our professionals have deep experience―not only assisting organizations in implementing and complying with information and cybersecurity requirements using NIST 800-53, NIST 800-171, DIACAP, ISO 27001, COBIT and other industry leading standards and frameworks―but also in implementing advanced breach detection solutions and cybersecurity technologies that align with industry standards.
ABOUT COHNREZNICK’S GOVERNMENT CONTRACTING PRACTICE
CohnReznick provides audit, tax, and advisory services to the government contracting business community regardless of the agency you have contracts with. Our experience dates back more than 40 years. Having served government contractors from small to Fortune 100 companies in a range of industries, CohnReznick understands business risk and the need to align the right security strategy with business goals.

Bhavesh Vadhani
Contact
Let’s start a conversation about your company’s strategic goals and vision for the future.
Please fill all required fields*
Please verify your information and check to see if all require fields have been filled in.










